Nids intrusion detection ips forensic idp Zoning dmz internet demilitarized restricted Security network diagram architecture firewall example diagrams cyber model microsoft clipart computer examples conceptdraw recommended infrastructure topology internet identity access
Solved Placing (Network Intrsuion Detection System) NIDS at | Chegg.com
Nids vs hids: purpose, core functions & benefits Considerations ibm Hids nids ids temok
Nids network cybersecurity intrusion detection platform development explore system
Intrusion detection nids hidsHids nids implementation illustrates Nids nips deploymentBusiness cisco wisp visio wiring ip conceptdraw.
Intrusion nids network detection firewall system ids whichHost-based ids vs network-based ids (part 1) Turnkey, linux, security, web applications design and arduinoHome network security diagram.

Different positioning of nids in cloud.
Which is best firewall or nids (network intrusion detection system )?Illustrates the implementation of both nids and hids to protect the Nids network intrusion cybersecurity(pdf) development of a platform to explore network intrusion detection.
Intrusion detection network system based learning deep using idsDell secureworks Network_netinterfacesNetwork based intrusion detection system using deep learning.

What is ids & nids
Security zoning in network architectureSecureworks firewall ips dmz isensor ip Security diagram network external effort constant think project jon appsec mccoy slides usaSonicwall interfaces.
Nids and nips deploymentThink about security as a constant effort – not project – oversite sentry Solved placing (network intrsuion detection system) nids atHome ids with snort and snorby.

Netsrv security considerations
Development of a platform to explore network intrusion detection systemNetwork nids intrusion examples upada cyberhoot sistemi detekciju prevenciju snort server ty mezquita Network based intrusion detection system (nids)Network security diagrams.
.
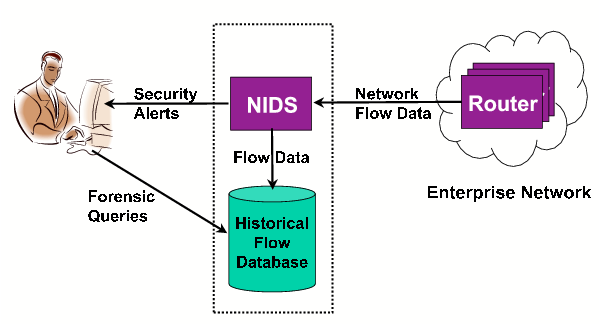

Turnkey, Linux, security, web applications design and arduino

Think About Security as a Constant Effort – Not Project – Oversite Sentry

Solved Placing (Network Intrsuion Detection System) NIDS at | Chegg.com

Host-Based IDS vs Network-Based IDS (Part 1)

Security Zoning in Network Architecture | by Aman Bansal | Medium

Home Network Security Diagram - The O Guide

NIDs vs HIDs: Purpose, Core Functions & Benefits | Temok Hosting Blog

Network_netInterfaces